Enterprise Data Security Solutions Guide
Enterprise data security solutions are the digital watchdogs and armored vaults built to protect a company's most valuable asset—its data. This isn't just a single piece of software; it's a complete, multi-layered strategy designed to guard information no matter where it is, whether it's sitting on a server, flying across the network, or being actively used by your team.
Why Data Security Is the Bedrock of Modern Business
In a world powered by information, data has become the new currency. For any large organization, protecting this currency isn't an optional extra—it's a non-negotiable requirement for survival and growth. Enterprise data security solutions provide the framework for that protection, going far beyond a simple antivirus or firewall. They represent a strategic promise to maintain the trust of customers, partners, and employees.
That promise is built on three core pillars, often called the CIA triad:
- Confidentiality: This makes sure data is only seen by authorized people. Think of it as a digital vault where only those with the right key can get in.
- Integrity: This guarantees your data is accurate and trustworthy by preventing unauthorized changes. It's the assurance that the information you're relying on hasn't been secretly altered.
- Availability: This ensures that authorized users can get to the data whenever they need it. It’s all about keeping your systems up and running so business doesn't grind to a halt.
More Than Just Technology
A common mistake is thinking enterprise security is just about buying the latest and greatest tools. While technology is a huge piece of the puzzle, a true solution weaves together people, processes, and technology into a unified defense. Even the most advanced software is useless without clear policies and well-trained employees. Sound data management best practices are the foundation you need before you can even think about building a security strategy on top.
The real goal of an enterprise security program isn't to build an impenetrable fortress—that's impossible. It's to create a resilient organization that can withstand and recover from attacks quickly. It's about managing risk, not trying to eliminate it completely.
This forward-thinking approach is more necessary than ever. As threats get smarter, businesses are spending big to keep up. Worldwide cybersecurity spending is projected to hit around $212 billion in 2025, a massive 15.1% jump from the previous year. Large enterprises are driving this spending, making up over 65% of the market because they have so much more to lose from both a financial and regulatory standpoint. You can dig into more cybersecurity spending forecasts from Cyvent. This huge investment highlights a simple truth: protecting your data is protecting your business.
Core Components of a Modern Security Fortress
Building a strong security posture is a lot like constructing a medieval fortress. You wouldn't rely on just one tall wall, right? You’d need multiple, layered defenses—a moat, a drawbridge, watchtowers, and guards—all working together. In the same way, a truly robust enterprise data security solution isn't a single product. It’s a collection of specialized technologies that team up to protect your digital assets.
These components create a cohesive defense, making sure that if one layer is somehow bypassed, another is right there waiting to stop a potential threat. Each technology has a very specific job, from guarding the digital perimeter to protecting the data itself.
This infographic breaks down how a modern "digital fortress" protects data no matter where it is—whether it's sitting on a server (at rest), traveling across a network (in motion), or being actively worked on (in use).
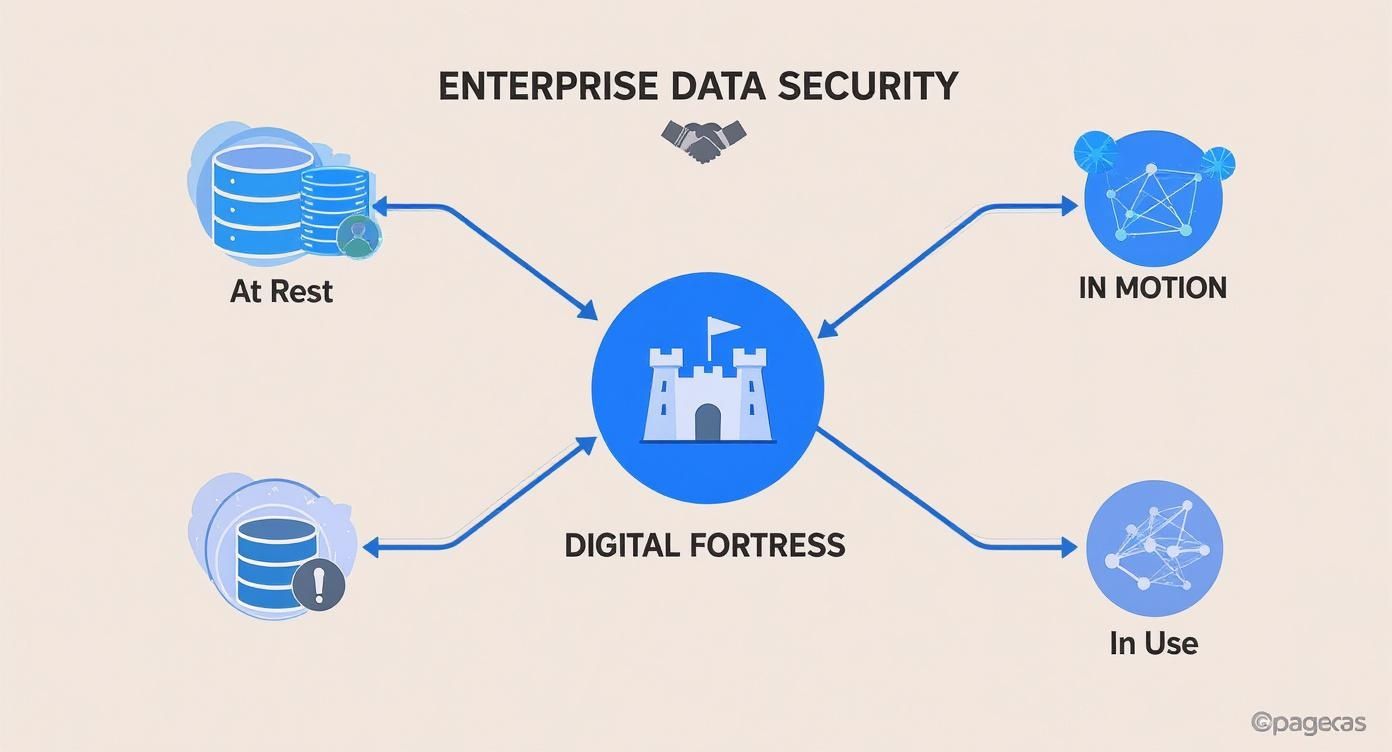
The key takeaway here is that a complete security strategy has to apply protections wherever data lives, not just where it's stored.
To help you get a clearer picture of these moving parts, here’s a quick look at the core technologies and what they do in the real world.
Key Enterprise Data Security Technologies at a Glance
| Technology Component | Primary Function | Example Use Case |
|---|---|---|
| Data Loss Prevention (DLP) | Monitors and blocks the unauthorized movement of sensitive data. | An employee tries to email a customer list to their personal account. DLP blocks the email and alerts the security team. |
| Identity & Access Management (IAM) | Ensures only the right people can access the right resources. | A junior marketing associate is prevented from accessing sensitive financial records because their role doesn't require it. |
| Encryption | Scrambles data into an unreadable format without the proper key. | A company laptop is stolen. The thief can't access any of the files because the hard drive is fully encrypted. |
| Security Info & Event Mgmt (SIEM) | Centralizes and analyzes security data to detect threats. | The SIEM flags thousands of failed login attempts on a single account from an unusual location, signaling a brute-force attack. |
These technologies aren't just buzzwords; they're the essential building blocks of any serious defense strategy. Let’s break down what each one actually does.
Data Loss Prevention: The Digital Gatekeeper
Think of Data Loss Prevention (DLP) solutions as your network's hyper-vigilant gatekeepers. Their entire job is to identify, monitor, and protect sensitive data from leaving your organization, whether someone is trying to sneak it out on purpose or just makes an honest mistake.
Imagine a security guard at the exit of a top-secret research lab who inspects every single package leaving the building. That's DLP. These systems use predefined policies to spot confidential information—things like credit card numbers, intellectual property, or patient health records.
If an employee tries to upload a proprietary design file to a personal cloud account or copy a sensitive client list to a USB drive, the DLP solution can step in, block the action, and notify an administrator. This is absolutely critical for staying compliant with regulations and protecting your company’s secret sauce.
Identity And Access Management: The Bouncer
If DLP is the gatekeeper, then Identity and Access Management (IAM) is the sharp, no-nonsense bouncer at the door of an exclusive club. IAM is all about making sure only authorized people can get in and that they stick to the approved areas. It boils down to two simple questions: Who are you? (authentication) and What are you allowed to do? (authorization).
Modern IAM systems are built on the principle of least privilege, which is a fancy way of saying people only get the bare minimum access they need to do their jobs—and nothing more.
Key features you’ll almost always find in an IAM solution include:
- Multi-Factor Authentication (MFA): This requires you to provide two or more pieces of evidence to prove you are who you say you are. It’s the single biggest reason why stolen passwords have become less of a catastrophe.
- Single Sign-On (SSO): Lets you log in once with a single ID and password to get access to multiple different applications. It’s a huge win for user experience that doesn't compromise on security.
- Role-Based Access Control (RBAC): Permissions are assigned based on a person’s job role in the company. This makes managing who-gets-what so much simpler.
By controlling access so tightly, IAM solutions form a foundational layer of defense that stops unauthorized users from ever getting near sensitive data in the first place.
A strong IAM framework doesn't just keep bad actors out; it ensures that even trusted insiders can't accidentally wander into areas where they don't belong, reducing the internal threat surface significantly.
Encryption: The Unbreakable Code
Encryption is the art of scrambling data into an unreadable code, making it completely useless to anyone who doesn't have the secret key to unlock it. It’s the digital version of writing a sensitive message in a secret language that only the intended recipient can understand. Honestly, it’s a non-negotiable part of any serious security setup.
Encryption is vital for protecting data in all three of its states:
- Data at Rest: Securing information just sitting on servers, in databases, or on laptops.
- Data in Motion: Protecting data as it zips across the internet or through your internal network.
- Data in Use: New technologies are even emerging to protect data while it’s actively being processed in a computer’s memory.
Ultimately, effective encryption is your last line of defense. If a cybercriminal manages to steal a server out of your data center or intercept your network traffic, the encrypted data remains safe and sound. With data volumes exploding, the market for securing it all was valued at USD 39.87 billion in 2024 and is projected to hit nearly USD 180 billion by 2033. This massive growth just goes to show how urgent the need is for strong encryption.
SIEM: The Central Command Center
Finally, we have the Security Information and Event Management (SIEM) system, which acts as the central command center for your entire security operation. It pulls in, sorts through, and analyzes log data from every corner of your IT environment—firewalls, servers, applications, and all the devices your employees use.
Imagine a security control room with screens showing feeds from hundreds of cameras. A SIEM is the intelligent system that watches all of those feeds at once, connects the dots between seemingly unrelated events, and spots suspicious patterns that could signal a cyberattack.
For example, it could flag multiple failed login attempts for one user, immediately followed by a successful login from a different continent, as a likely account takeover. By giving security teams a single dashboard for monitoring and threat detection, SIEMs help them respond to incidents way faster and more effectively. This is often where Global Standards like ISO 27001 and AI-powered risk detection are monitored and managed, tying all the pieces of your security strategy together.
How to Choose the Right Data Security Solution
Picking the right enterprise data security solution isn't like buying off-the-shelf software. It’s more like choosing a long-term business partner. This decision will have far-reaching consequences, so you have to move beyond a simple feature checklist.
The best solution for another company might be a terrible fit for you. The real goal is to find a system that aligns with your unique operational realities, risk profile, and future goals.
Think of it as designing a custom security system for your specific business. You wouldn't use the same blueprint for a bank vault and a retail store, right? In the same way, your security needs will depend entirely on the kind of data you handle, your industry's regulations, and the complexity of your IT environment. That requires a thoughtful look at several key factors.
Conduct a Thorough Risk Assessment
Before you even look at a single vendor, you need to know exactly what you're protecting and what you're protecting it from. A comprehensive risk assessment is the absolute foundation of this entire process. It all starts with identifying your most valuable data assets—the "crown jewels" of your organization.
This process should give you clear answers to a few critical questions:
- What is our most sensitive data? This could be anything from customer financial information and intellectual property to employee health records.
- Where does this data live? Is it tucked away on-premise servers, scattered across multiple cloud services, or sitting on employee laptops?
- What are our biggest threats? Are you more worried about external hackers, accidental insider leaks, or sophisticated ransomware attacks?
By mapping out your critical assets and pinpointing your specific vulnerabilities, you create a clear roadmap. This ensures you invest in protection that solves your actual problems instead of buying a generic solution with features you’ll never use.
A detailed risk assessment shifts the conversation from "What does this product do?" to "How does this product solve our specific security problems?" This focus is the difference between purchasing technology and building a true security strategy.
Evaluate Scalability and Future Growth
Your business isn’t static, and your security solution can't be either. Scalability is a massive factor. It determines whether the solution can grow with your organization or if you'll be forced into a costly and disruptive replacement down the line. A solution that works perfectly for 500 employees might completely buckle under the pressure of 5,000.
When you’re looking at scalability, consider these angles:
- User and Device Growth: Can the system seamlessly handle a big jump in users, endpoints, and servers without grinding to a halt?
- Data Volume Expansion: As your data footprint inevitably expands, will the solution be able to monitor, analyze, and protect it all effectively?
- Geographic Expansion: If you’re planning to open new offices in different regions, can the solution provide consistent protection and policy enforcement everywhere?
Choosing a scalable solution is a direct investment in your company's future. It gives you the flexibility to adapt to market changes, acquisitions, or organic growth, making sure your security posture stays strong as your business evolves.
Prioritize Seamless Integration Capabilities
Modern companies run on a diverse ecosystem of technologies, from cloud platforms like AWS and Azure to legacy on-premise applications. A truly effective data security solution has to be a team player, integrating smoothly with the IT infrastructure you already have. A tool that operates in a silo just creates blind spots and management nightmares.
Look for solutions with robust APIs and pre-built connectors for the tools you already rely on. This integration is vital for creating a unified security fabric where information flows freely between systems. For example, integrating your security tool with your HR system can automate the process of revoking access when an employee leaves the company—instantly closing a common security gap.
Strong integration gives you a holistic view of your security posture instead of a fragmented one. It simplifies administration, cuts down on manual work for your IT team, and ultimately leads to a more effective and responsive defense.
Calculate the Total Cost of Ownership
At the end of the day, a solution that isn't financially sustainable isn't a solution at all. The initial purchase price is just one piece of the puzzle. To make an informed decision, you have to calculate the Total Cost of Ownership (TCO), which covers all the direct and indirect costs over the solution's entire lifespan.
TCO includes several components that go way beyond the sticker price:
- Implementation and Setup Fees: The costs tied to professional services for deployment and configuration.
- Annual Licensing and Maintenance: Ongoing subscription or support fees needed to keep the software up-to-date.
- Hardware Requirements: Any new servers or appliances required to run the solution.
- Training and Personnel: The cost of getting your team trained to manage the system, plus any potential need for new hires with specialized skills.
By analyzing the TCO, you get a realistic picture of the long-term financial commitment. This allows you to choose a data security solution that is not only technologically sound but also fits your budget, preventing surprise costs and ensuring the program’s viability for years to come.
Comparing On-Premise, Cloud, and Hybrid Models
Choosing your data security tools is only half the battle. Deciding where those tools will live—on-premise, in the cloud, or a mix of both—is just as critical. This choice directly shapes your costs, control, scalability, and who’s on the hook for maintenance.
Think of it like getting electricity for your house. You could build your own power plant in the backyard (on-premise), pay a utility company for power (cloud), or install solar panels that are supplemented by the main grid (hybrid). Each path has its own trade-offs, and the right one depends entirely on your needs.
Let's break down these models so you can figure out which one best fits your company's reality.
The On-Premise Model: Maximum Control
On-premise is the old-school approach. You buy all the hardware and software yourself and run it out of your own data centers. This gives you absolute, granular control over every single piece of your security setup, from who can physically touch the servers to how the network is configured.
This level of control isn't just a preference; it’s often a hard requirement for businesses in heavily regulated fields like finance or healthcare. When compliance rules say data can't leave a specific physical location, on-premise is the only way to go.
But that control doesn't come free. On-premise solutions require a hefty upfront investment in hardware and software licenses. Plus, your own IT team is responsible for everything: maintenance, patching, upgrades, and troubleshooting. It’s a big lift.
The Cloud-Based (SaaS) Model: Ultimate Flexibility
At the other end of the spectrum is the cloud-based or Software-as-a-Service (SaaS) model. Here, you offload the entire infrastructure headache to a third-party provider. You just subscribe to the service and access it over the internet. No hardware, no data centers, no fuss.
This approach is all about flexibility and speed. The benefits are pretty compelling:
- Lower Initial Costs: Forget massive capital expenses. You’re just paying a predictable subscription fee.
- Rapid Deployment: Getting started is usually as simple as signing up and running through a configuration wizard. You can be up and running in hours, not months.
- Automatic Updates: The provider handles all the maintenance and patches behind the scenes, so you’re always on the latest, most secure version.
The main trade-off here is trust. You're handing your security data over to a third party, which means you have to do your homework and make sure their security and compliance measures are rock-solid.
A cloud-based model lets you focus on security strategy, not infrastructure management. You get to stop worrying about keeping the lights on and start focusing on higher-level security goals.
The Hybrid Model: A Balanced Strategy
What if you want the control of on-premise for some things but the flexibility of the cloud for others? That's where the hybrid model comes in. It’s a pragmatic “best of both worlds” approach that lets you mix and match.
For instance, a company might keep its crown jewels—like core intellectual property—on-premise for maximum security but use a cloud-based service for email filtering or endpoint protection. This lets you align your security posture with the actual risk level of your data.
A hybrid setup is a fantastic way to modernize your security without ripping and replacing everything at once. It’s also a natural stepping stone for organizations that eventually want to move fully to the cloud, allowing them to migrate workloads piece by piece.
Of course, managing a split environment requires a solid game plan, especially for data protection. It's crucial to have comprehensive data backup strategies that seamlessly cover both your on-premise and cloud assets.
Ultimately, there’s no single right answer. The best model for you depends on your budget, regulatory needs, and the skills of your team. By weighing these factors, you can build a security foundation that truly protects your organization.
Best Practices for Implementation and Management
Picking the right enterprise data security solution is a huge step, but it’s really just the starting line. The real payoff from your investment comes from a thoughtful implementation and disciplined, ongoing management. Just flipping the switch on new technology without a plan is like buying a state-of-the-art alarm system but never arming it.
To turn your tools into a truly resilient security program, you need a framework of processes and policies that actually guide how they’re used.
It all begins with a comprehensive data governance policy. This isn't some dusty technical document; it's the official rulebook for your entire organization. It needs to clearly define who can access what data, under what circumstances, and why. This creates a baseline for accountability and ensures security is applied evenly, not just in pockets.
Develop a Phased Rollout Plan
Trying a "big bang" implementation—where you turn everything on at once—is a classic recipe for disrupting the entire business. A phased rollout is a much smarter and safer way to go. This approach lets you introduce new security controls in manageable stages, which dramatically minimizes the impact on day-to-day work.
A staged approach gives your team time to adjust and provides valuable opportunities to gather feedback. More importantly, it allows you to iron out any technical wrinkles before they can affect the whole company. Start with a non-critical department or a specific dataset to pilot the new solution. This creates a controlled environment where you can test policies, train a core group of users, and build positive momentum for the full deployment.
Foster a Security-First Culture Through Training
Your employees are your first line of defense, but without the right training, they can easily become your weakest link. The only way to close that gap is with continuous, engaging training. This has to be more than a once-a-year slideshow; it’s about cultivating a security-first mindset where every single employee understands their role in protecting company data.
An effective training program should include:
- Regular Phishing Simulations: These teach employees how to spot and report malicious emails in a safe, controlled way.
- Policy Education: Make sure everyone understands the rules for handling data, including crucial procedures for secure file transfers. For more on this, check out our guide on file transfer best practices.
- Incident Response Drills: Practice makes perfect. Running drills on what to do during a breach ensures the real response is swift and effective, not chaotic.
Security isn't just an IT problem; it's a fundamental business responsibility. When employees understand the 'why' behind the rules, they're far more likely to become active partners in the company's defense instead of seeing security as just another roadblock.
Embrace Security as a Continuous Process
The threat landscape is always shifting, which means your security posture can't afford to stand still. Data security is an ongoing cycle of assessment, adaptation, and improvement—it’s not a one-and-done project. This proactive stance is what separates the organizations that bounce back from the ones that get breached.
This continuous loop involves several key activities:
- Regular Audits and Vulnerability Assessments: Systematically scan your systems for weaknesses and verify that your security controls are actually working as intended.
- Policy Reviews and Updates: Your data governance policies should be living documents, updated regularly to reflect new tech, changing business processes, and new regulations.
- Incident Response Planning: Develop a detailed incident response plan and—just as importantly—rehearse it regularly so your team knows exactly what to do when something goes wrong.
This kind of proactive management is more critical than ever. The global market for data-centric security was valued at USD 4.28 billion in 2022 and is projected to hit USD 24.01 billion by 2030, a clear sign of the intense pressure to protect sensitive information. For a deeper look at protecting your assets, exploring these essential data security best practices will provide valuable insights.
Unsurprisingly, sectors like banking and finance are leading the charge, making up 26% of the market, as they remain prime targets for cyberattacks.
The Future of Enterprise Data Security
The world of enterprise data security never stands still. To stay ahead, you have to look past today's threats and get ready for what’s coming over the horizon. The future isn't about building higher walls; it’s about creating smarter, more adaptive defenses that can see trouble coming and shut it down before it even starts.
This evolution is being supercharged by Artificial Intelligence (AI) and Machine Learning (ML). These technologies are completely rewriting the rulebook for threat detection. Instead of just matching threats against a list of known "bad guys," AI-powered systems dig through mountains of network data to figure out what normal, everyday activity looks like. That way, they can instantly spot weird behavior that signals a new or hidden attack.
This flips the script from reactive to proactive security. For instance, an ML algorithm could pick up on the faint, tell-tale signs of a brewing ransomware attack and automatically quarantine the affected systems before a single file gets encrypted.
The Rise of Zero Trust
Another massive shift happening right now is the move to a Zero Trust architecture. This whole model is built on one beautifully simple idea: never trust, always verify. It throws out the old, outdated concept of a "safe" internal network and a "dangerous" outside world.
In a Zero Trust framework, every single user and device has to prove who they are and that they have permission to access a resource—every single time. It’s like having to show a key and an ID to get into every room in a building, not just the front door.
This approach dramatically shrinks the "attack surface." If a hacker somehow gets a foothold in one corner of the network, they're trapped. They can't move sideways to get to the crown jewels. It’s becoming a non-negotiable foundation for any modern enterprise data security solution.
Preparing for Emerging Challenges
Looking even further out, new technologies are bringing both incredible opportunities and serious challenges. Quantum computing, for example, is a looming threat to our current encryption standards. These powerhouse machines will one day be able to crack them wide open, so organizations need to start thinking about a move to quantum-resistant cryptography.
At the same time, Privacy-Enhancing Technologies (PETs) are becoming more critical. These tools let businesses analyze and share insights from data without ever exposing the raw, sensitive information itself. It’s a way to get value from data while navigating a minefield of privacy regulations. Keeping an eye on these developments is the only way to build a security strategy that's truly built to last.
Frequently Asked Questions
When you're wading into the world of enterprise data security, a lot of practical questions come up. Here are some clear, straightforward answers to the most common ones we hear from organizations trying to button up their digital defenses.
What Is the First Step in Building a Data Security Strategy?
The very first move is always a thorough risk assessment. Before you can protect anything, you have to know what you have, where it is, and what you're up against.
This foundational step is all about mapping your most critical information—your "crown jewels"—and figuring out where the weak spots are. It’s the only way to get the clarity you need to spend your security budget wisely. This ensures you’re focusing resources on shielding your most valuable assets from your most likely threats, instead of just grabbing a generic, one-size-fits-all solution off the shelf. Without this crucial first step, any security strategy is just guesswork.
How Do These Solutions Help with Regulatory Compliance?
Think of these tools as the bedrock of your compliance efforts. Regulations like the General Data Protection Regulation (GDPR) and the Health Insurance Portability and Accountability Act (HIPAA) don't just ask you to protect data—they demand it, with specific rules for handling personal and sensitive information.
Enterprise data security solutions are what make meeting those demands possible. They help you tick the boxes in a few key ways:
- Access Controls: Identity and Access Management (IAM) tools are the gatekeepers, making sure only authorized people can touch regulated data. This is a core requirement of nearly every privacy law out there.
- Data Monitoring: Data Loss Prevention (DLP) systems keep an eye on how sensitive information is being used and shared, stopping unauthorized transfers that could land you in hot water with regulators.
- Encryption: Scrambling data, whether it’s sitting on a server or flying across the internet, is a standard requirement. It's your best defense in a breach and helps you meet your legal obligations.
- Audit Trails: Security Information and Event Management (SIEM) systems create detailed, verifiable logs of all data activity. When auditors come knocking, this is the proof you need to show you’ve done your due diligence.
By putting these tools in place, you’re building a technical framework that automatically enforces your compliance policies.
Think of these security tools as automated compliance officers. They work around the clock to enforce the rules defined by regulations like GDPR, providing the technical evidence needed to demonstrate due diligence to auditors.
Are Enterprise Solutions Suitable for Small Businesses?
Absolutely. The word "enterprise" might bring to mind massive corporations, but that’s not the whole story anymore. Many of today's best data security solutions were built with scalability in mind, making top-tier protection accessible to businesses of all sizes.
Cloud-based (SaaS) solutions, in particular, have completely changed the game. They’ve lowered the barrier to entry by getting rid of the need for a huge upfront investment in hardware. Instead, you get a subscription-based model that can grow right alongside your business. This flexibility means smaller companies can get the same high-level protection as their larger competitors, tailored to fit their exact budget and needs.
Ready to secure your digital assets without sacrificing performance? Compresto helps you prepare files for secure sharing by compressing them directly on your Mac, ensuring they never leave your device. Learn more about fast, private, and powerful compression with Compresto.